How Secure Is Trainual?
Learn how Trainual keeps your data safe and secure.
Security is at the forefront of everything we do here at Trainual. We proactively seek ways to secure the application and improve our overall security posture.
Trainual ensures that all internal employees understand and participate in securing the platform, and everyone at Trainual is involved in developing, implementing, and complying with internal security policies.
👉 A few quick facts:
-png.png?width=688&height=341&name=image%20(7)-png.png)
Learn more about Trainual's policies:
🗂️ Table of contents: Skip around to just the parts you need with these links.
- SOC 2 compliance.
- Trainual’s security cornerstone: Zero trust architecture.
- Database security layer: Protecting your data.
- Network security layer: Protecting communications.
- Endpoint and server security layer: Intrusion detection & anti-malware.
- Codebase security layer: Supply chain protection.
- Security research.
- Have additional questions? Contact us!
- Learn more about Trainual.
SOC 2 compliance:
📝 Please note: When you move forward with an Enterprise Trainual plan, you can request access to all SOC 2 documentation from us. Learn how to upgrade here.
Trainual’s security cornerstone — Zero trust architecture:
The Trainual approach to cybersecurity has been developed through a lens of zero trust to ensure protection of the entire security surface. The security team here applies a layered approach to threat modeling and implements specific security controls in each of the identified layers.
Further security access to your Trainual account can be implemented by using single sign-on (SSO) through integrated providers like Okta, Microsoft Entra, and Google, to help manage identity and authentication more efficiently.
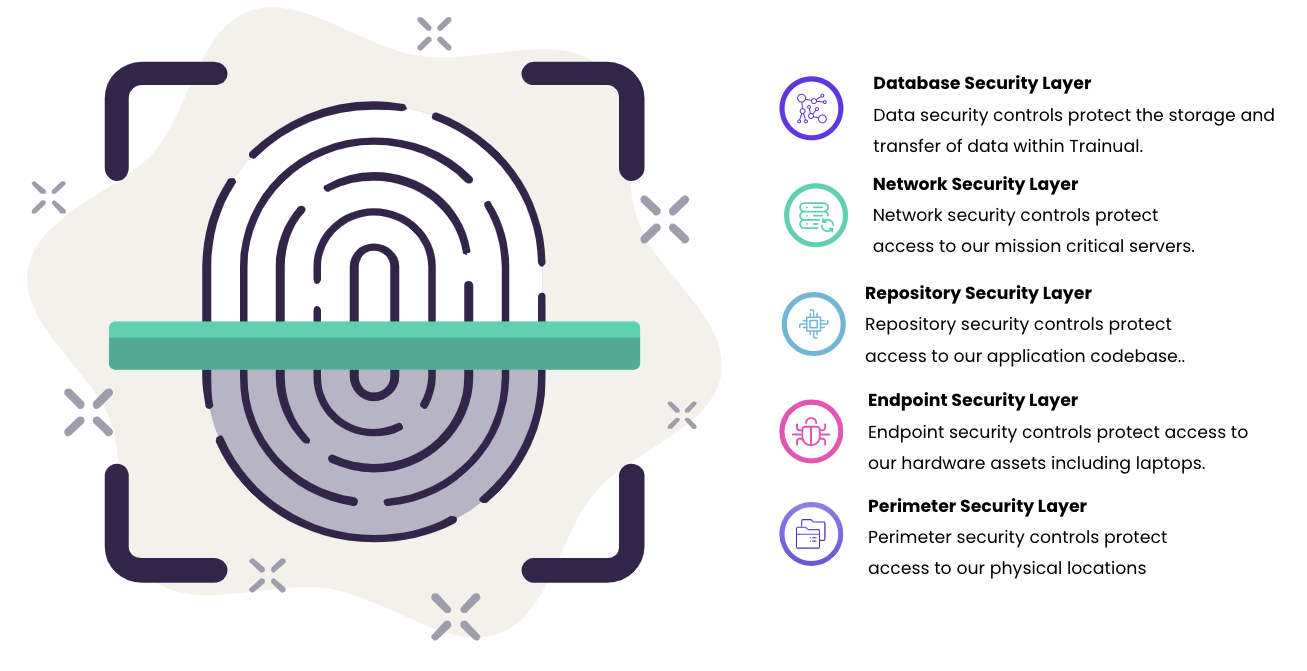
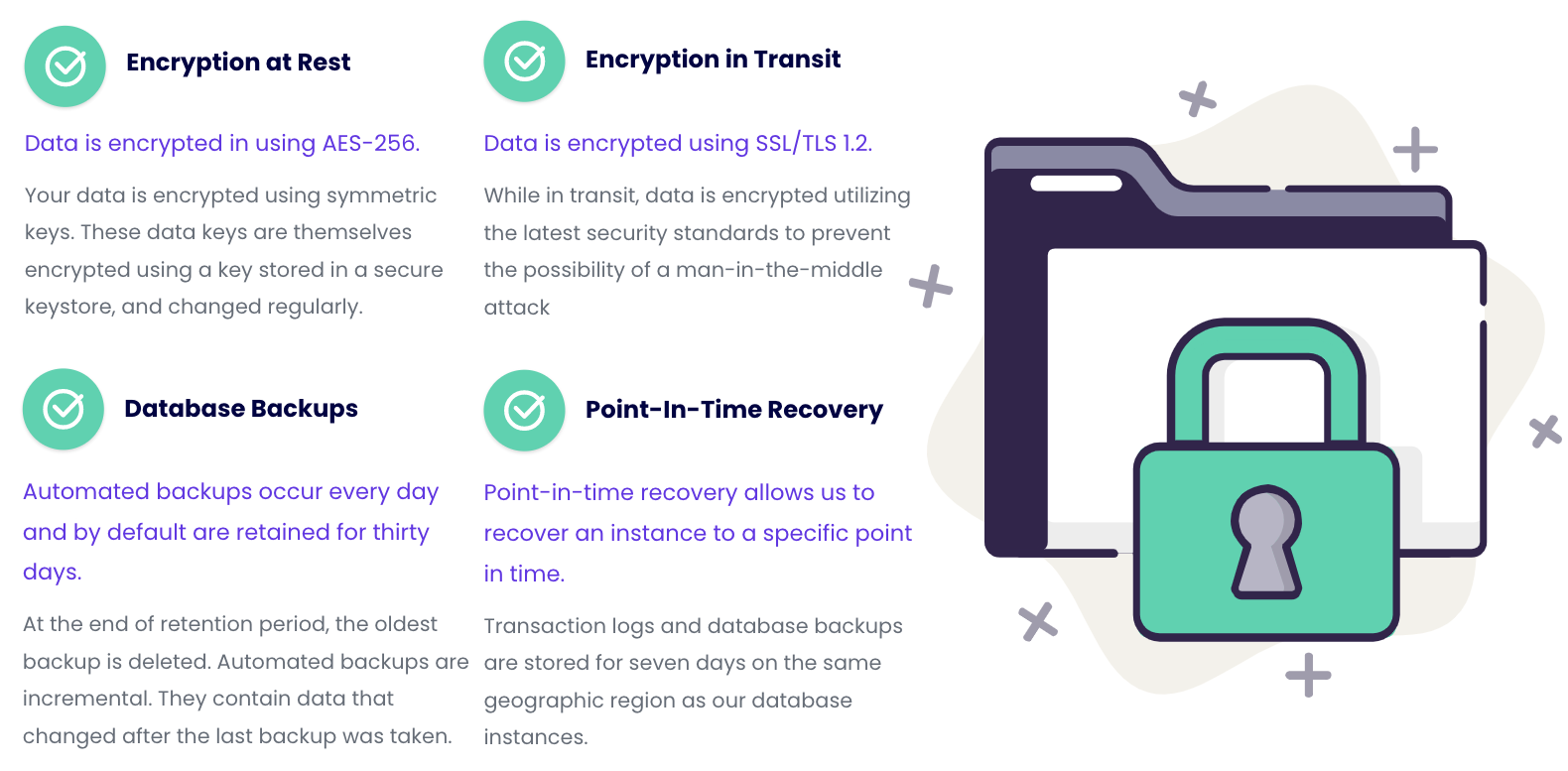
Database security layer — protecting your data:
All data is encrypted in transit and at rest, and stored on PCI Level 1 compliant servers with daily automated backups. Our infrastructure is hosted on Google Cloud Storage (GCS), which is known for its top-tier security protocols and they are PCI-DSS, ISO 27000, and SOC 1-2-3 compliant.
🔍 Learn more about the Cloud Providers:
-
Google Cloud's Compliance Resource Center.
-
Amazon Web Services (AWS) PCI DSS Information.
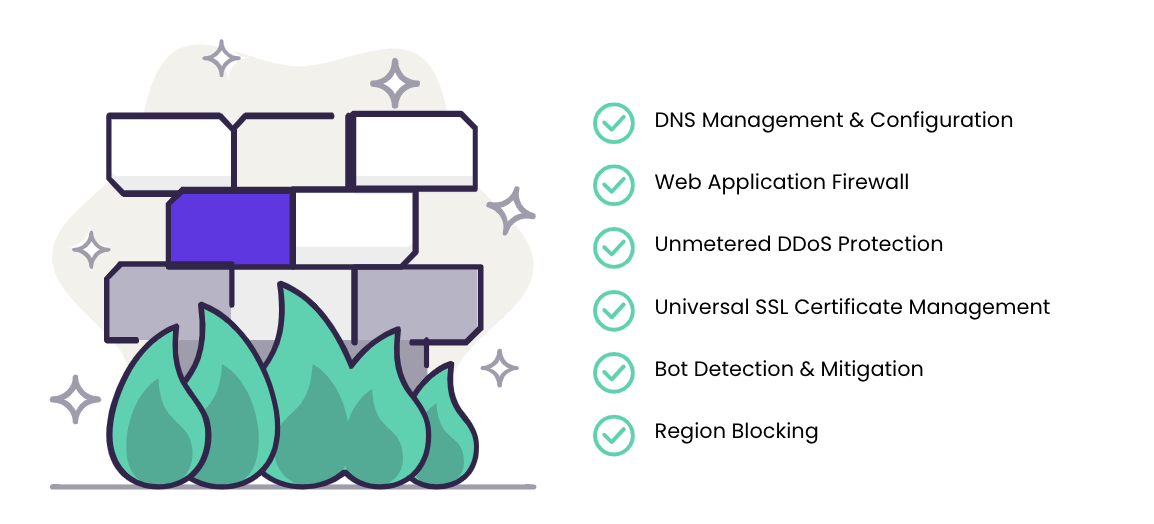
Network security layer — protecting communications:
Trainual utilizes Cloudflare as the core network security provider. Cloudflare stops brute-force attacks and hacking attempts, filtering out most of the spam attacks at the DNS level so that they don't even hit Trainual’s server. Cloudflare protects Trainual websites from DDOS attacks, SQL injections, comment spam, and more.
Endpoint and server security layer — intrusion detection &
anti-malware system:
Trainual's next-generation antivirus (NGAV) system provides unmatched prevention capabilities, protecting against malware, ransomware, fileless, and even malware-free attacks. The threat intelligence integration immediately assesses the origin, impact, and severity of threats in the environment and provides recovery guidance for decisive incident response and remediation.
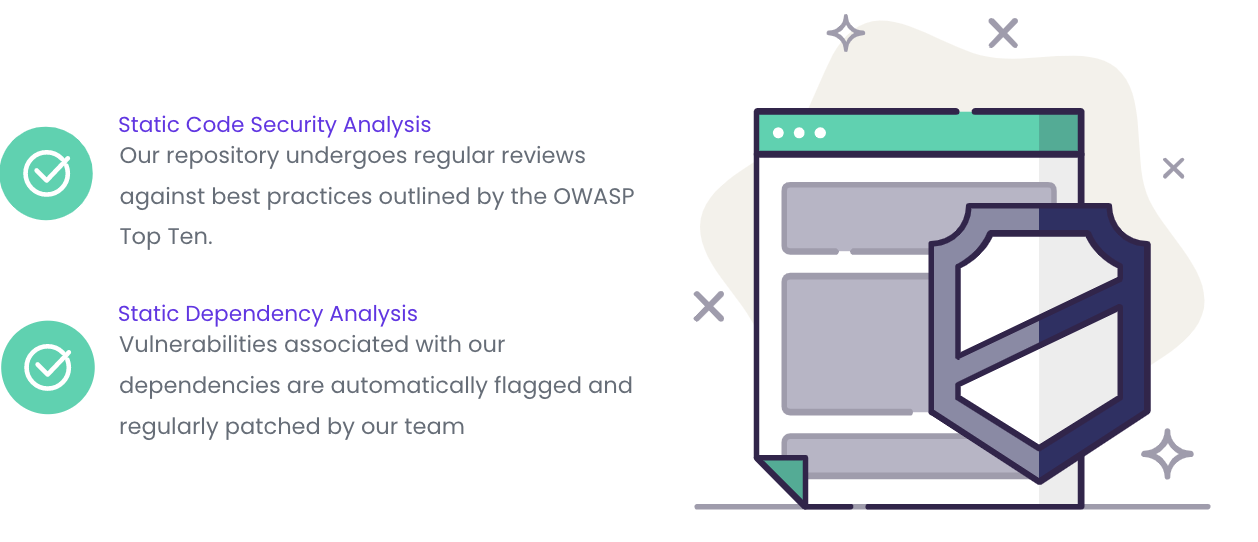
Codebase security layer — supply chain protection:
Trainual is regularly undergoing analysis to adjust to the changing security landscape. The application has been built on a modern technical stack and is constantly being updated as new vulnerabilities are discovered within the broader security community.
Security research:
Trainual is committed to taking action from reports submitted by independent security researchers and immediately patching any security findings.
If requested, Trainual will give public credit for these reported findings, as long as the supporting research is bound to our Responsible Disclosure Agreement, and follows the guidelines stated in the document.
Have additional questions?
Email security@trainual.com or press on the bubble on the bottom right-hand corner of the screen to start a chat with Support to let us know how we can help. ↘️
Learn more about Trainual:
- Find out if Trainual meets your team's present and future needs.
- Is Trainual HIPAA compliant?
- Is Trainual SCORM compliant?